Managing Cyber Security
The ingredients for cybersecurity management begin with the assessment process (Identify) and ends with implementing compliance tools and recommendations found in RiskTool to build or enhance your cybersecurity strategy (Recover). They include securing your network (Protect), installing security programming (Detect), and a strategy for incidents (Respond).
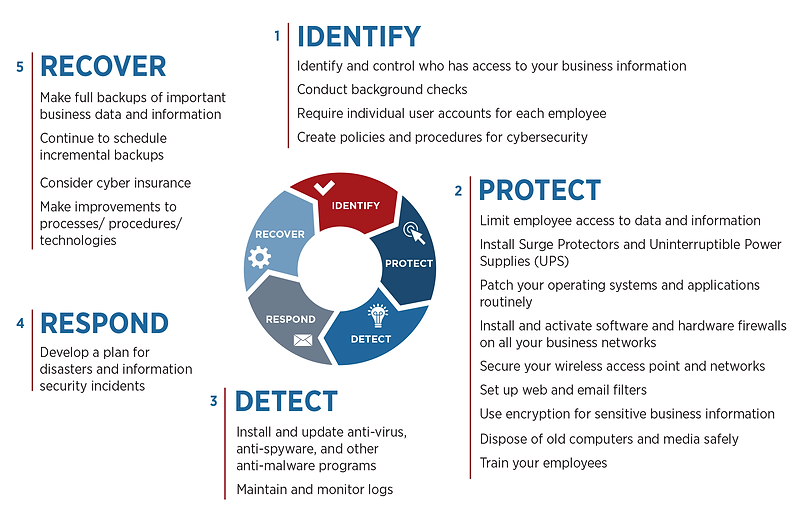
Identify
The power of conducting assessments and inspections
The basis for spending any money (resources) on cybersecurity is understanding what information you’re trying to protect. Obviously, some information is more important than others and could be regulated. Answering various questions about how vulnerable that information (the important and regulated ones) is to potentially being exposed, is the key to setting an overall cybersecurity strategy. An assessment will provide a list of factors that influence vulnerability. Things such as network infrastructure, trade secrets, customer data, access, asset management, and other factors are weighted which set priorities. We apply a score in order to measure the actions that will make the greatest impact on improving that number. Inspections are designed to establish a course of action, work plan if you will, that can be followed to address compliance, education, or infrastructure needs.
Protect
To protect is to act.
It is the process of implementing various control measures to be in compliance and reduce risk. RiskTool is a Platform for Solution Providers and direct customers. We provide a collaborative solution to deliver expertise regarding how to apply access control measures to the organization. Policies and procedures are established and communicated to the population of users regarding how networks will be protected, including an array of choices for locking down sensitive information and keeping users protected from criminal efforts to obtain data/information. We support managed service providers so they may deliver the depth and breadth of this solution to their customers. Our system is fully complemented by a host of training videos for providing knowledge and documenting compliance efforts.
Detect
How do you measure the effectiveness of your current cybersecurity culture?
Our platform is usually privately labeled and seamlessly integrated with other software solutions. Recently, we have introduced the ability to create email campaigns that test the effectiveness of your training programs and the understanding your employee population has toward the policies that have been implemented. This is not intended to be used as a way to expose and intimidate, but rather a tool to be used to show just how important it is to be careful, and seek guidance. This tool is coupled with a service to monitor the dark web for possible infiltration and exposure. These capabilities are a powerful and effective way to substantiate your cybersecurity culture.
Respond
Incident Response and Disaster Recovery
The time to address when to prepare for the inevitable event that may expose protected information, is not after it happens. We have helped literally thousands of businesses plan and implement strategies to avoid business disruption. Our solution gives you control over the event so you are managing it rather than it managing you. Obtaining accurate information and being able to communicate effectively is key to bringing an event to resolution.
Recover
RiskTool guides you through the regulatory rules process.
In order for you to demonstrate the due diligence expected of your organization such as documenting the existence of assessments, written programs, policies, procedures, and training, RiskTool gives your organization a centralized place where all levels of employees including executives can obtain the necessary information to manage cyber risk.
RiskTool Can Help With Competitive Insurance Rates
Many companies purchase insurance to transfer the risk. It stands to reason that a company that demonstrates they are actively seeking to lower their vulnerability to perceived risks, should pay lower premiums. RiskTool can be used as a collaborative platform to exchange information and demonstrate your actions to lower risk with your carrier. Give your broker and underwriter the ammunition to get you the most competitive rates possible!
